Protecting Public Data and Trust with Azure Security and Microsoft Entra – A State DOJ Case
On June 27, 2022 – California Department of Justice launched a new Firearms Dashboard Portal with altruistic intentions to “improve transparency and information sharing for firearms-related data” and “balance its duties to provide gun violence and firearms data to support research efforts while protecting the personal identifying information in the data the Department collects and maintains”. Fast forward less than 30 days, the Attorney General’s office is now being sued by two different parties, a national non-profit on July 1 and a group of four CA citizens on July 18 respectively. Both lawsuits are predicated on the assumption that the bold text was not upheld.
The CA DOJ and the CA Attorney General are not alone in facing the three pressures that incited this particular incident.
- Citizens want greater transparency when it comes to community health data, criminal activity, and other politically impacted domains like firearm ownership.
- This data comes in many forms (databases, video footage, internal reports/memos, court documents, etc.) and resides on a broad array of digital locations.
- This data is of special interest to hackers looking to leverage Personal Identifiable Information (PII) for financial gain OR hacktivists desiring to expose a particular truth or perceived truth by leaking the information to the broader public.
As of this writing, we do not know fully what the data source was, where it was hosted, its architecture, preventative measures that were in place, or the attack vector used. Regardless, State/City/County CIOs and CISOs have the task to protect and govern this data throughout its lifecycle no matter where the data resides. Thus, the internal conversations happening across DOJs and other agencies throughout the country are centered around preventing similar data and financial loss. Budgets and personnel resources are not easy to come by for mitigation efforts; thus, one avenue worth exploring is simplification and unification of data governance. Below is a discussion on how organizations can more effectively prevent these types of attacks through the use of multiple Azure Security capabilities and Microsoft Entra.
Perfection Isn’t the Goal – Awareness Is
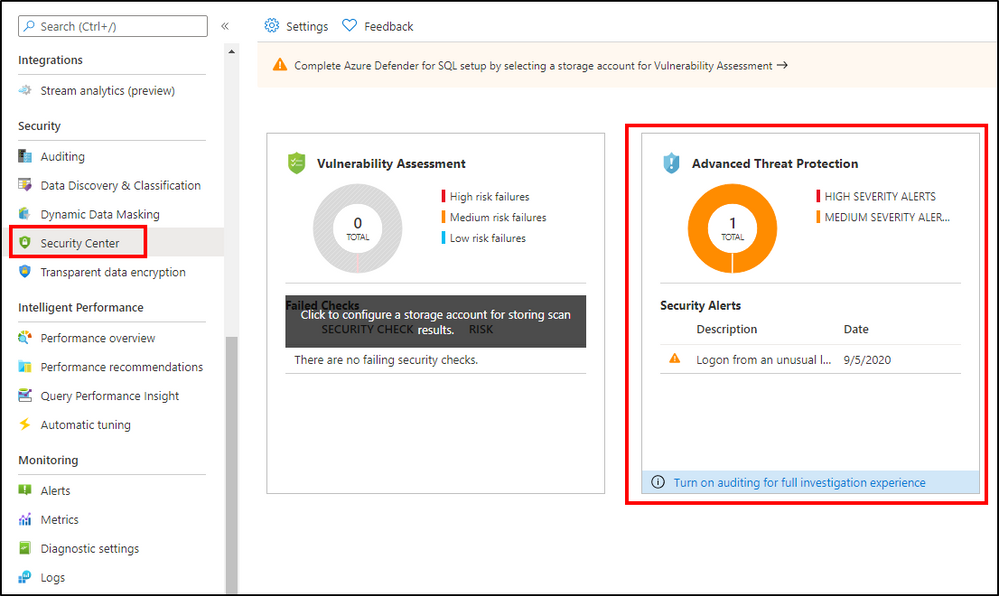
Threats to expose or steal data assets like State held PII can come in the form of network-based attacks, compromised identities, insider threats, and more. To help detect some of these threats and the vulnerabilities they exploit, Microsoft Defender for SQL (if the data lives in a SQL environment) provides a native assessment capability that can be performed at a single moment in time or established as a weekly cadence. The service scans for necessary patches, poorly configured settings, excessive permissions for users, and other baseline management functions.
Beyond mitigating static vulnerabilities via periodic assessments, you can actively monitor your SQL instance with Microsoft Defender’s Advanced Threat Protection capabilities for persistent threats causing havoc in your account. Security analysts can inspect alerts of potential brute force SQL credentials, access from unusual locations or a dormant account, access from an unfamiliar IP address or potentially harmful application, and unusual exports from an authorized user or exfiltration with DNS tunneling. Other subtle threats can also be detected where users may elevate their privileges or the privileges of others, indicating possible horizontal movement or malicious intent.
Authentication and Access – The Costco Method
If you’ve visited your local Costco in the last decade, your experience has been a derivative of the following events:
- Walk in and show your Costco ID/shopper card (which they typically never validate is you)
- Shop and partake in as many food samples as possible
- Scan your Costco ID/shopper card to begin scanning items and checkout
- Hand over receipt for inspection of your cart to validate what you have is what you paid for, and a magic sharpie signifies you can leave
- Go home and explain to your partner why you needed the family sized Doritos bag and a 4x Pack of emergency flashlights
Just like your average Costco experience wherein Costco defines the conditions for accessing, interacting with, and leaving with the consumer goods in its stores – an organization like a State Department of Justice or City/County government should restrict internal user access to sensitive citizen information by a well-defined set of conditions. The emphasis is on internal user access because often attacks can come in the form of a user identity that is being manipulated or used by an external party. This is ironically similar to the Costco card that is often wielded by a family member or friend, who is in fact not a real Costco member. #MembersOnly
A State Agency or City/County CISO often will define how they protect a particular data set by who they want to access the data, how they want these users to access it, and what the extent of their access entails. For conversation’s sake, let’s assume the underlying data for a public information portal was in a SQL database in Azure Government as stated previously. The first check at the door would be enabling multifactor authentication via Azure Active Directory (AAD), a component of Microsoft Entra. Secondly, it is not enough that a user can authenticate with their username/password and other factors like the use of Microsoft’s Authenticator App. Organizations should consider deploying Conditional Access Policies via AAD to control what devices a user can authenticate from and where they can login from.
Moreover, with Microsoft Entra’s Role Based Access Control (RBAC) you can control what resources can be accessed by which user and what actions they can perform. You can also limit VM access to just-in-time through other capabilities in Azure, which allows admins to do only the work that needs to be done in a certain time frame.
Just like Costco, it’s important to have more than one mitigation in place to protect critical assets and the spicy hot deals on patio furniture.
Protecting Sensitive Data – Governments with Ungoverned Data
Microsoft Purview (previously known as Azure Purview) can be deployed to manage multiple data sources in Azure like in this example, other cloud infrastructure, or on premises. Using Microsoft Purview Data Map, an administrator can create a collection that can be permission trimmed to a specific set of users or groups. Moreover, the individuals in the organization that can alter or change Microsoft Purview policies can also be governed by specific roles within the governance portal.
For most of the blog, we’ve focused primarily on sensitive PII data living on server infrastructure in Azure (IaaS). Yet, as evidenced by multiple premature releases of judicial and legislative decisions causing great political and civil impact, not all sensitive information lives on a SQL server. Sensitive memo’s, discussions about new legislation, government research, video footage, and case files are stored and acted upon within Microsoft 365 applications. Microsoft Purview in Microsoft 365 allows a State DOJ to label sensitive content manually or automatically in Exchange, OneDrive, Teams, PowerBI, etc.
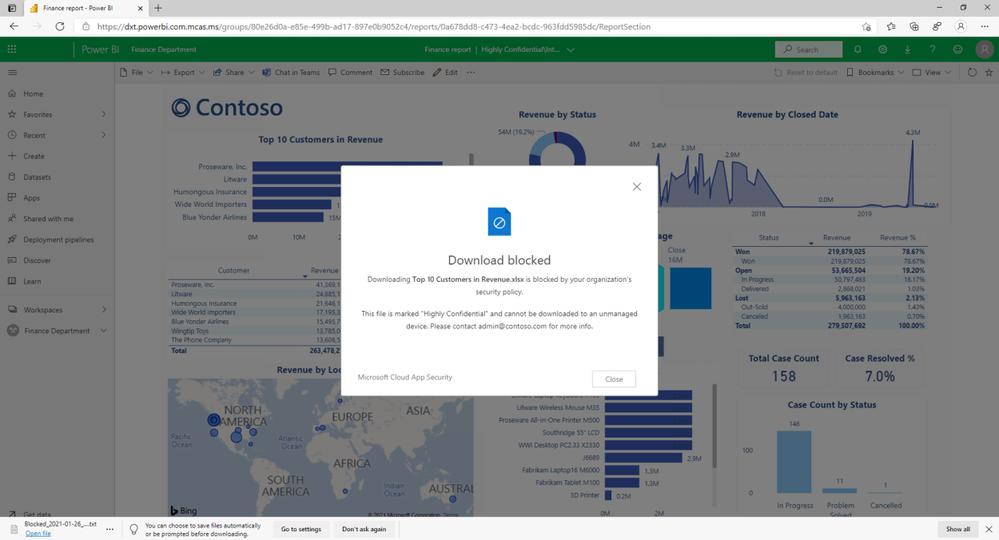
With sensitivity labeling and the power of other native capabilities like Data Loss Prevention (DLP) and Microsoft Cloud App Security (MCAS), users will be unable to copy and paste or distribute sensitive information to unintended audiences/applications. Also, printing and downloading functionality can be limited by these solutions to prevent other forms of data exfiltration.
Transparency – The Opportunity and Cyber Issue Facing Every State DOJ
The amount and types of data being shared with the public will continue to grow and change respectively. Therefore, CIOs and CISOs will need to be closely aligned as more agencies try to meet the demand of their citizens without indirectly impacting citizen privacy or the safety of public officials. Cybersecurity grants will continue to aid in the investments necessary to protect this data; however, resourcing will continue to be a gap for the foreseeable future.
Therefore, technology can help alleviate some of the administrative burden of protecting this data. DOJs or the supporting State OIT will need a wholistic platform approach appropriate visibility for incident response and vulnerability management on these data sources, multilayered zero trust strategies for authentication, and native data labeling and governance across wide-ranging applications. Deploying these solutions will not prevent all attacks or cover every threat vector (for example this article does not address firewall solutions). Yet, it may be prudent to start with a comprehensive platform strategy to integrate other mitigating solutions in at a later point in your plan of action and milestones.